Conference Program
IFIP SEC 2015, IFIPTM 2015, WISE 9, Workshop on Assurance & Control, Workshop on Information Security Management
Presenters should prepare their talk to last a maximum of 20 minutes to allow sufficient time for discussion. Short papers will have 10-15 minutes for presentation.
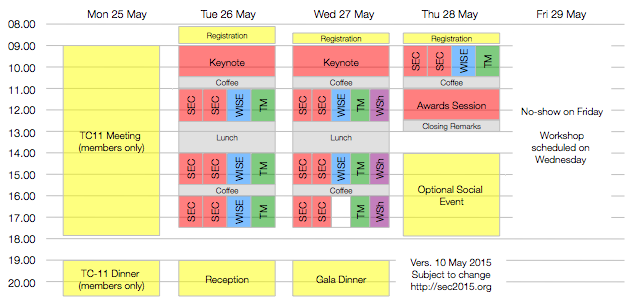
25 May 2015 (Monday)
| 09:00 | TC-11 Meeting (IFIP TC-11 members only)
121W
|
|
| 12:30 | Lunch Break | |
| 14:00 | TC-11 Meeting | |
| 18:00 | TC-11 Meeting End | |
| 19:00 | TC-11 Dinner (IFIP TC-11 members only) | |
26 May 2015 (Tuesday)
| 08:00 | Registration
First Floor
|
|
| 09:00 | IFIP SEC 2015 Opening | 221W |
IFIP SEC Invited Talk |
||
| 10:30 | Coffee Break
Ground Floor
|
|
| 11:00 | Parallel Session 1a: IFIP SEC (Privacy I, Chair: Jaap-Henk Hoepman) O-PSI: Delegated Private Set Intersection on Outsourced Datasets Flexible and Robust Privacy-Preserving Implicit Authentication Towards Relations between the Hitting-Set Attack and the Statistical Disclosure Attack |
121W |
| 11:00 | Parallel Session 1b: IFIP SEC (Web Security, Chair: Carlos Rieder) Cache Timing Attacks revisited: efficient and repeatable browser history, OS and network sniffing Enforcing Usage Constraints on Credentials for Web Applications A Survey of Alerting Websites: Risks and Solutions |
221W |
| 11:00 | Parallel Session 1c: WISE (Tools and Applications for Teaching, Chair: Matt Bishop) Welcome by IFIP WG 11.8 Chair – Lynn Futcher Learn To Spot Phishing URLs with the Android NoPhish App An Innovative Approach in Digital Forensic Education and Training: the EduFors Tool On Experience of Using Distance Learning Technologies for Teaching Cryptology |
220W |
| 11:00 | Parallel Session 1d: IFIPTM (Short Papers) 1,2, pause: Lets start by meaningfully navigating the current online authentication solutions space Data Confidentiality in Cloud Storage Protocol based on Secret Sharing Scheme: A brute force ajack evaluation The Detail of Trusted Messages: Retweets in a Context of Health and Fitness Reusable Defense Components for Online Reputation Systems Continuous Context-Aware Device Comfort Evaluation Method |
120W |
| 12:30 | Lunch Break
Ground Floor
|
|
| 13:30 | IFIP WG 11.11 Meeting
120W
|
|
| 14:00 | Parallel Session 2a: IFIP SEC (Privacy II, Chair: Bart De Decker) POSN: A Personal Online Social Network Strategic Noninterference Verifying Observational Determinism |
121W |
| 14:00 | Parallel Session 2b: IFIP SEC (Mobile and Cloud Services Security I, Chair: Nathan Clarke) ApkCombiner: Combining Multiple Android Apps to Support Inter-AppAnalysis Assessment of the Susceptibility to Data Manipulation of Android Games with In-app Purchases An Empirical Study on Android for Saving Non-shared Data on Public Storage |
221W |
| 14:00 | Parallel Session 2c: WISE Panel Discussion: Building National Cybersecurity Workforces |
220W |
| 14:30 | Parallel Session 2d: IFIPTM IFIPTM Keynote on Data Protection by Marit Hansen (ULD Kiel) |
120W |
| 15:30 | Coffee Break
Ground Floor
|
|
| 16:00 | Parallel Session 3a: IFIP SEC (Security Management and Human Aspects of Security I, Chair: Ingrid Schaumüller-Bichl) Social groupings and information security obedience within organizations Attack Trees with Sequential Conjunction Enhancing the Security of Image CAPTCHAs through Noise Addition |
121W |
| 16:00 | Parallel Session 3b: IFIP SEC (Mobile and Cloud Services Security II, Chair: Leon Strous) The Dual-Execution-Environment Approach: Analysis and Comparative Evaluation On the Privacy, Security and Safety of Blood Pressure and Diabetes Apps A Cloud-based eHealth Architecture for Privacy Preserving Data Integration |
221W |
| 16:00 | Parallel Session 3c: WISE (Software Security Education, Chair: Erik Moore) Cybersecurity through Secure Software Development Security Injections 2.0: Increasing Engagement and Faculty Adoption using Enhanced Secure Coding Modules for Lower-level Programming Courses The Use of Software Design Patterns to Teach Secure Software Design: an Integrated approach |
220W |
| 16:00 | Parallel Session 3d: IFIPTM Tutorial / Panel on Data Protection |
120W |
| 18:15 | Bus transfer from Dammtor (Shell gas station, REISERING buses) to Reception at Town Hall. Alternatively, you can walk or use public transport. See the program book in your conference bag for instructions. | |
| 19:00 | Reception (“Senatsempfang”) with drinks and Finger Food: Hamburg Town Hall, Rathausmarkt 1, 20095 Hamburg Appropriate attire (business formal or business casual) expected, but not enforced strictly. Please remember to bring your invitation card and passport with you. |
|
27 May 2015 (Wednesday)
| 08:30 | Registration
First Floor
|
|
| 09:00 | IFIP SEC Invited Talk |
221W |
| 10:30 | Coffee Break
Ground Floor
|
|
| 11:00 | Parallel Session 4a: IFIP SEC (Applied Cryptography, Chair: Dominik Herrmann) Fast Revocation of Attribute-Based Credentials for Both Users and Verifiers Chaotic Chebyshev polynomials based remote user authentication scheme in client-server environment A Secure Exam Protocol Without Trusted Parties |
121W |
| 11:00 | Parallel Session 4b: IFIP SEC (Software Security I, Chair: André Zúquete) SHRIFT System-wide HybRid Information Flow Tracking ISboxing: an Instruction Substitution based Data Sandboxing for x86 Untrusted Libraries Exploit Generation for Information Flow Leaks in Object-Oriented Programs |
221W |
| 11:00 | Parallel Session 4c: WISE (Innovative Methods, Chair: Natalia Miloslavskaya) Realism in Teaching Cybersecurity Research: The Agile Research Process Assurance Cases as a Didactic Tool for Information Security Cognitive Task Analysis Based Training for Cyber Situation Awareness A Cyber Security Multi Agency Collaboration for Rapid Response That Uses AGILE Methods on an Education Infrastructure |
220W |
| 11:00 | Parallel Session 4d: IFIPTM (Authentication) Mathematical Modeling of Trust Issues in Federated Idenity Management Simple and Practical Integrity Models for Binaries and Files Enabling NAME-based security and trust |
120W |
| 11:00 | Parallel Session 4e: Workshop on Assurance & Control / Workshop on Information Security Management Welcome by Workshop co-chairs - Abbas Shahim / Gurpreet Dhillon and Karen Hedstrom Information assurance Keynote on Audit & Trust in cloud environments |
223W |
| 12:30 | Lunch Break
Ground Floor
|
|
| 14:00 | Parallel Session 5a: IFIP SEC (Access Control, Trust and Identity Management I, Chair: Dogan Kesdogan) A Generalization of ISO/IEC 24761 to Enhance Remote Authentication with Trusted Product at Claimant Enhancing Passwords Security using Deceptive Covert Communication Information Sharing and User Privacy in the Third-party Identity Management Landscape |
121W |
| 14:00 | Parallel Session 5b: IFIP SEC (Software Security II, Chair: Hannes Federrath) Memoized Semantics-Based Binary Diffing with Application to Malware Lineage Inference Mitigating Code-Reuse Attacks on CISC Architectures in a Hardware Approach Integrity for Approximate Joins on Untrusted Computational Servers |
221W |
| 14:00 | Parallel Session 5c: WISE (Syllabus Design, Chair: Lynn Futcher) Reflections on the Ethical Content of the IT honours Program Project Module Professional Competencies Level Assessment for Training of Masters in Information Security History of Cryptography in Syllabus on Information Security Training |
220W |
| 14:00 | Parallel Session 5d: IFIPTM (Privacy) Trust Driven Strategies for Privacy by Design Lightweight practical private one-way anonymous messaging Privacy-Preserving Reputation Mechanism: A Usable Solution Handling Negative Ratings |
120W |
| 14:00 | Parallel Session 5e: Workshop on Assurance & Control / Workshop on Information Security Management Security Operations Center Investigating Cloud Storage Security Requirements and Critical Controls End user development and information security culture |
223W |
| 15:30 | Coffee Break
Ground Floor
|
|
| 16:00 | Parallel Session 6a: IFIP SEC (Access Control, Trust and Identity Management II, Chair: Simone Fischer-Hübner) An Iterative Algorithm for Reputation Aggregation in Multi-dimensional and Multinomial Rating Systems A Comparison of PHY-Based Fingerprinting Methods Used to Enhance Network Access Control Model-driven Integration and Analysis of Access-control Policies in Multi-layer Information Systems |
121W |
| 16:00 | Parallel Session 6b: IFIP SEC (Network Security, Chair: Kai Rannenberg) Authenticated File Broadcast Protocol Automated Classification of C&C Connections through Malware URL Clustering B.Hive: A Zero Configuration Forms Honeypot for Productive Web Applications |
221W |
| 16:00 | Parallel Session 6d: IFIPTM (Trust in Online Collaboration) Obscuring Provenance Confidential Information via Graph Transformation Social Network Culture Needs the Lens of Critical Trust Research Predicting Quality of Crowdsourced Annotations using Graph Kernels An Architecture for Trustworthy Open Data Services |
120W |
| 16:00 | Parallel Session 6e: Workshop on Assurance & Control / Workshop on Information Security Management IT audit and financial statement review Secure and Privacy Focused Customer Device Management in a Smart Household Environment |
223W |
| 18:15 | Bus transfer from Dammtor (Shell gas station, REISERING buses) to Gala Dinner. Alternatively, you can use public transport. See the program book in your conference bag for instructions. | |
| 19:00 | Gala Dinner: Lutter & Wegner, Große Elbstraße 49, 22767 Hamburg Bring your badge / dinner ticket! |
|
| 21:30 | Early Bus from Restaurant back to Dammtor | |
| 22:30 | Late Bus from Restaurant back to Dammtor | |
| 23:00 | End of Gala Dinner; you can use public transport (Bus 112) from Hafentreppe or Fischmarkt bus stops to get back to Dammtor station. | |
28 May 2015 (Thursday)
| 08:30 | Registration
First Floor
|
|
| 09:00 | Parallel Session 7a: IFIP SEC (Security Management and Human Aspects of Security II, Chair: Philippos Peleties) Investigation of Employee Security Behaviour: A Grounded Theory Approach Practice-Based Discourse Analysis of InfoSec Policies Understanding Collaborative Challenges in IT Security Preparedness Exercises |
121W |
| 09:00 | Parallel Session 7b: IFIP SEC (Cyber-physical Systems and Critical Infrastructures Security, Chair: Peter Lambert) Application of a Game Theoretic Approach in Smart Sensor Data Trustworthiness Problems Securing BACnet’s Pitfalls On the secure distribution of vendor-specific keys in deployment scenarios |
221W |
| 09:00 | Parallel Session 7c: WISE WG 11.8 meeting (All IFIP WG 11.8 members) and WISE9 Closing |
220W |
| 09:00 | Parallel Session 7d: IFIPTM (Towards Trustworthy Cloud Infrastructures) A Cloud Orchestrator for deploying public services on the cloud — the case of STRATEGIC project Integrating Security Services in Cloud Service Stores Building an Eco-System of Trusted Services via user Control and Transparency on Personal Data Security-as-a-Service in Multi-cloud and Federated Cloud Environments The role of SLAs in building a Trusted Cloud for Europe |
120W |
| 10:30 | Coffee Break
Ground Floor
|
|
| 11:00 | IFIP SEC 2015 Awards Session | 221W |
|
Video message from the Kristian Beckman Award 2015 winner (download MOV file, 575 MB)
IFIP SEC 2015 Best Student Paper Award
Reputation – from Social Perception to Internet Security
|
||
| 12:30 | IFIP SEC 2015 Closing Remarks | 221W |
| 12:30 | IFIPTM 2015 Closing Remarks | 221W |
| 14:30 | Optional Social Event: Waterways trip “Fleetfahrt” Boat departs from Jungfernstieg at the waterfront (pier number will be announced on Wednesday at the registration desk). Important notes: You have to sign up for the social event at the registration desk. There is no organized transfer from SEC venue. There is no lunch on the boat and no space for large pieces of luggage. |
|
| 16:30 | End of optional Social Event Boat returns to Jungfernstieg. |
|
29 May 2015 (Friday)
| Important note: The Workshop on Information Security Management is now scheduled on 27 May 2015 (Wednesday) 16:00-17:30. | ||
